- Published on
CWL - Compute Crack
- Authors

- Name
- mfkrypt

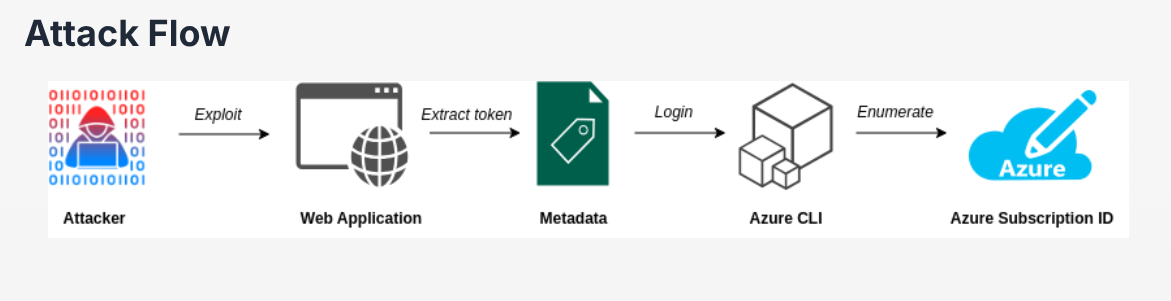
Table of Contents
Recon
Upon browsing to the target, we are met with a webpage that has a form request
Let us enter some data and observe the response in burp
After a bit of testing we discover the organization parameter is also vulnerable to Command Injection
Given that the challenge is about Azure SSRF, we can try to curl the internal 169.254.169.254 to access the Instance Metadata Service (IMDS). More about what this IP address is in my previous post. We also would need the Metadata header to be set to True in order for the query to work.
The curl command would be:
curl -H "Metadata: True" "http://169.254.169.254/metadata"
According to the docs, these are API versions that can be accessed to retrieve the IMDS. I tested some of it and all of them gave the same output, so its just a matter of choosing one API version to append at the end of the command
The curl command would be:
curl -H "Metadata: True" "http://169.254.169.254/metadata/instance?api-version=2025-04-07"
Acquiring Subscription ID
We can pipe the output to python -m json.tool to parse the json and make it readable
Scrolling down we can see the subscriptionId field and value
Disclaimer
I tried to solve it by using the PowerShell AzureAD Module and the az cli tool but I found out that it was impossible without an organization email. For the az cli tool I don't know why the access token I found on another endpoint was incorrect ...I could be wrong though. If anyone knows about this, you can reach out to me on Discord, mfkrypt